Your data, your money, your identity, and many other things depend on your passwords or keys. If it fails, the internet won’t forgive, and everything will be compromised. In this article, we will overview, explain, and compare three authentication methods: password, passkey, and seed phrase. Also, we’ll review the pros and cons of each of them, so you understand what’s keeping your money safe.
Password — OG of account protection
Everyone uses them, everyone has forgotten them, and some still use qwerty123. We can trace the history of passwords back to ancient times, when military watch required a password from those willing to pass into the guarded area. In the digital realm, passwords have been used since 1961, first applied on MIT’s shared computers.
Since then, the concept hasn’t changed significantly — the user chooses a secret word or phrase, and the computer hashes it (encrypts the password, making it easy to compute but impossible to reverse-engineer). Every time you log in, the system checks if the new hash matches the one in the database and decides whether you can sign in or not.
Why do we still use passwords?
- Simple and cost-effective to implement for developers.
- Supported everywhere — from legacy systems to modern devices.
- Password managers can generate and store strong, unique passwords for users.
- Adoption of other authentication methods is still in progress.
Why should we stop using passwords?
- Highly phishable — attackers can easily trick users into revealing them.
- Easy to forget or reuse across services, increasing security risks.
- Frequently exposed in data breaches, even when hashed.
- Increasingly outclassed by phishing-resistant alternatives like passkeys.
Passkey — safe zero-effort access
Are you tired of browsers asking if you want to “remember your password”? Well, passkeys are basically the same idea, but taken to the next level to be safer, smoother, and phishing-proof. Geeks would say that passkeys follow FIDO2/WebAuthn standards, but we’ll simply note that Apple, Google, and Microsoft have adopted passkeys and are forcing their implementation.
Passkey uses asymmetric cryptography. It may sound complex, but you know what it means — a passkey consists of private and public keys, where the public key is accessible to everyone, and the private key signs the messages and verifies that you are really you.
How passkey works:
- Key generation The first time you register, your device’s secure element (like trust platform module) creates a private-public key pair. The public key goes to the website; the private key never leaves your device.
- Challenge-response On login, the website sends a one-time challenge. Your device signs it with the private key. The server verifies it using the stored public key.
- Biometric unlock Fingerprint, Face ID, or a local PIN unlocks the key — none of this biometric data is ever sent to the server.
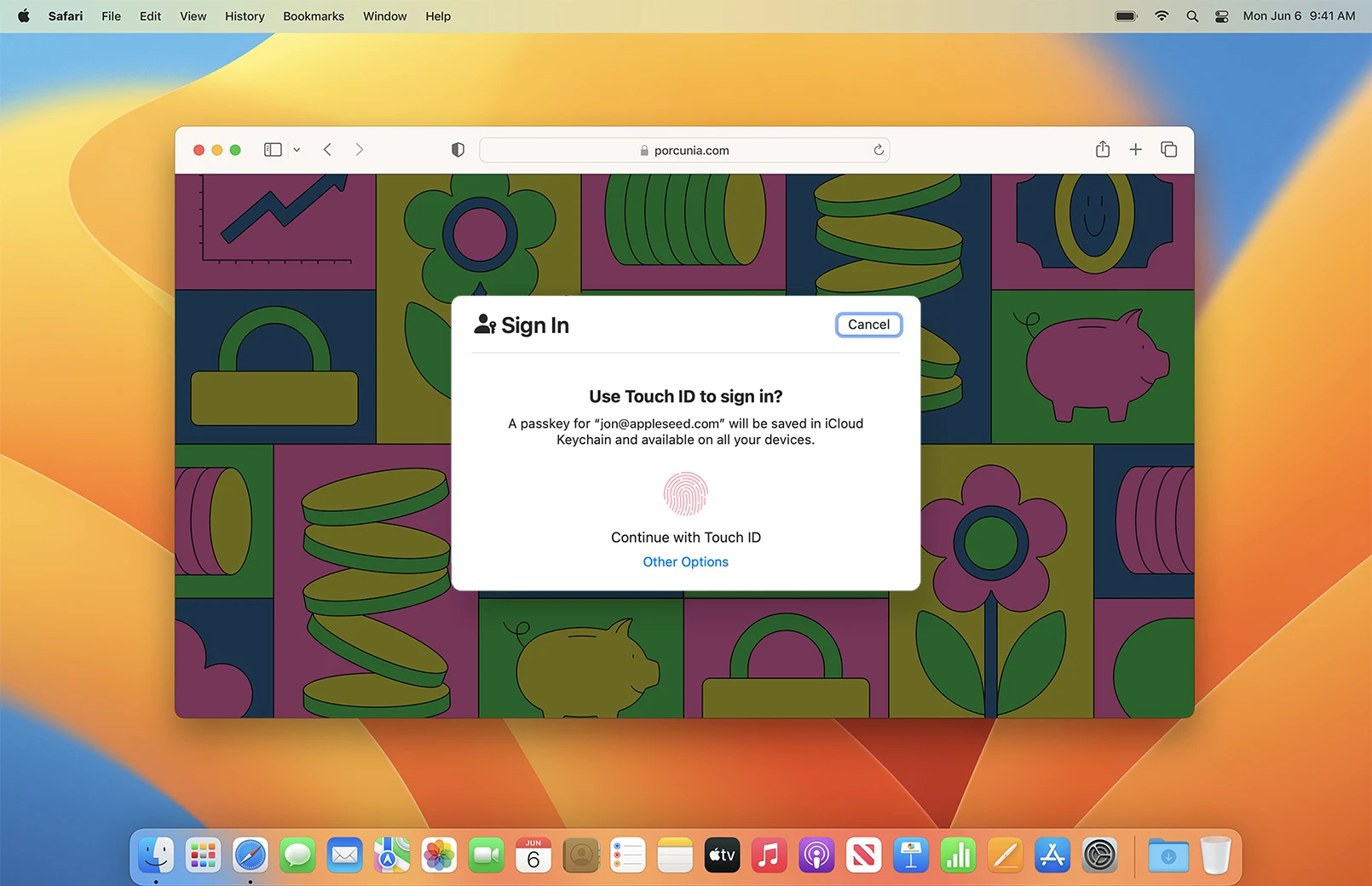
Are passkeys safer than passwords?
In short, yes, because passkeys are extremely hard to phish, as even users don’t really have easy access to their passkeys in a raw format. Also, passkeys are resistant to security breaches of third-party services, as users never share the private key. And they are literally unforgettable, as all you need for authentication is biometrics.
Yet, there are minor cons:
- If you don’t back up the keys from your local password manager (such as Apple Keychain or Google Password Manager), you risk becoming locked out and losing access to your services in case of device loss.
- The adoption of passkeys as a safer password alternative has just begun, and you can’t really use them on many websites and services.
Seed, phrase, as, crypto, alternative, to, passwords
Seed phrases are strange. A phrase from 12 to 24 words, like “zebra, pumpkin, lamp…,” is really meant to protect your holdings? Technically, it’s not. The recovery phrase is generated by your wallet, following the BIP-39 standard (Bitcoin Improvement Proposal 39). The phrase itself is not a key or password, but it is an encoded version of the private key of your wallet.
With it, you can fully restore your wallet and assets using any wallet or platform that supports import features. And this is the seed phrase’s superpower and supervulnerability.
So, the recovery phrase is not even stored anywhere. When you enter the sequence of words in the right way, you just recover your private key, which grants access to the assets in the wallet.

When one uses cold wallets, the private key and its seed phrase is not ever exposed to the internet. Additionally, it’s compatible with any non-custodial wallet, so you don’t have to rely on a third party. That’s cryptography magic.
Still, we’ll remind you about risks: Exposed phrase means stolen funds, forgotten phrase means lost funds. Forever.
A couple of words on 2FA
2FA, short for two‑factor authentication, adds a second layer of security on top of your password or passkey. It’s like asking for your ID after you unlock the door — just to be sure it’s really you.
There are a few types:
- SMS codes (least safe, but still better than nothing)
- Authenticator apps like Google Authenticator or Authy (time‑based codes that refresh every 30 seconds)
- Hardware tokens are the gold standard — plug it in or tap to verify yourself
Why use 2FA? Because even if someone steals your password (or, in rare cases, access to your passkey), they still can’t log in without the second factor.
Tip: Avoid SMS‑based 2FA if you can. SIM swapping attacks are real, and they’re getting nastier.
Which One Should You Trust?
That depends on the platform you're dealing with and the level of security you require.
For the web, you can safely use strong, unique passwords combined with two-factor authentication. It will be fast and acceptably safe if the account is not associated with any valuable assets or funds.
When it comes to fintech, passkeys are preferred because they offer a combination of top-tier security and minimal hassle, as all you have to do to log in is scan your face or fingerprint.
In crypto, you don’t usually have a choice. But if the app offers 2FA, passkeys and seed phrase — take it all, as you can’t be overprotected when your own assets are at stake.
In short:
- Passwords: Good enough for low-stakes use
- Passkeys: The new standard for secure, streamlined logins
- Seed phrases: High-risk, high-responsibility keys to financial sovereignty
Conclusion
Passwords are still everywhere because they’re easy to implement and universally supported, but they’ve proven time and again to be vulnerable and outdated.
Passkeys are backed by cryptography and biometrics, making them both safe and convenient. That’s why they are already replacing passwords on major platforms.
Meanwhile, seed phrases are usually associated with crypto wallets. They are really safe until they are exposed.
Each tool comes with its own strengths and trade-offs. Passwords offer flexibility but carry a high risk. Passkeys provide a seamless, phishing-proof alternative for web and app logins. Seed phrases grant absolute control in crypto, but with no safety once compromised.
Ultimately, your digital safety depends not only on the tool you use but also on how effectively you utilize it. Equip yourself accordingly.


